Data Security Firewall
Benefits

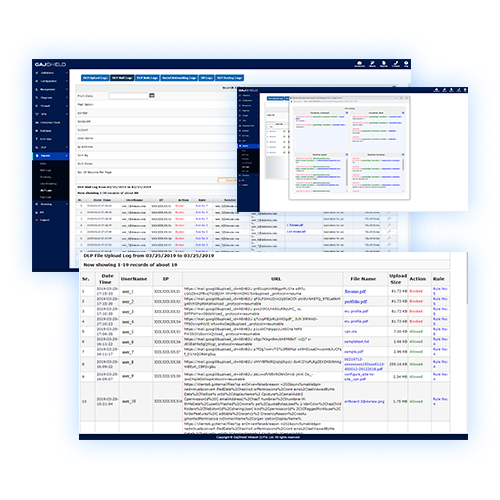
Data Security Health

Threat Surface Management

SaaS data Control

Data Visibility and control
Cloud based data security model for roaming users

Limit Social Media/ Collaborative Apps to Business Use only
Context sensitive data leak prevention

Advanced Contextual Data Classification
Our Approach
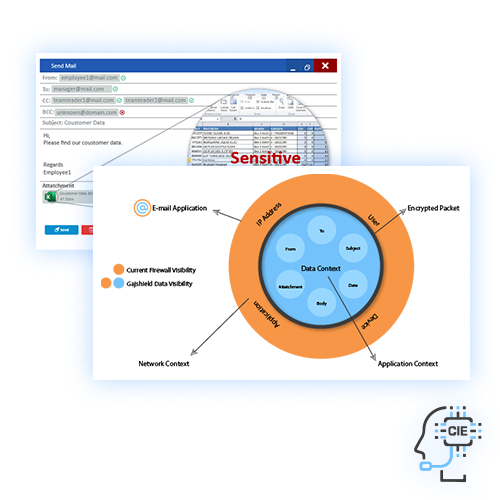
A Unique Context based
DATA LEAK PREVENTION
A Powerful
CONTEXTUAL INTELLIGENCE ENGINE
OUR BLOGS
"Truth or Fiction: Exploring the Era of Deep Fakes and Digital Deception"
Deepfake technology refers to the sophisticated use of artificial intelligence (AI) and machine learning techniques to create...
A Special Gift for Our Valued Customers: Three Months of GajShield firewall on Azure - On Us!
Gratitude Gesture At GajShield, we cherish our long-standing relationship with you, our valued customers. Your trust and loy...
GajShield granted patent for 'Data Leak Prevention from networks using Context Sensitive Firewall'
GajShield Infotech, a leading cybersecurity company, recently announced that it has been awarded the patent on "Data Leak Pre...
What Is Defense-in-depth Strategy and How Does it Aid with Cybersecurity?
We live in a world where digitization has become the way of life. Almost every individual now has a digital identity. However...
"Truth or Fiction: Exploring the Era of Deep Fakes and Digital Deception"
Deepfake technology refers to the sophisticated use of artificial intelligence (AI) and machine learning techniques to create...
A Special Gift for Our Valued Customers: Three Months of GajShield firewall on Azure - On Us!
Gratitude Gesture At GajShield, we cherish our long-standing relationship with you, our valued customers. Your trust and loy...
GajShield granted patent for 'Data Leak Prevention from networks using Context Sensitive Firewall'
GajShield Infotech, a leading cybersecurity company, recently announced that it has been awarded the patent on "Data Leak Pre...








