Data Security Firewall
A Firewall that understands data.
For Security Beyond just the perimeter
Read MoreData Security Firewall
Benefits

Data Security Health

Threat Surface Management

SaaS data Control

Data Visibility and control
Cloud based data security model for roaming users

Limit Social Media/ Collaborative Apps to Business Use only
Context sensitive data leak prevention

Advanced Contextual Data Classification
Our Approach
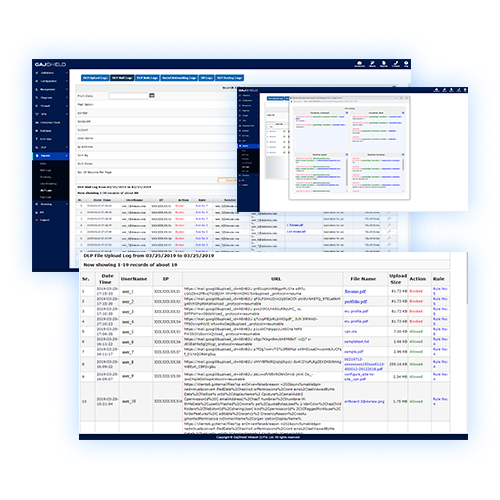
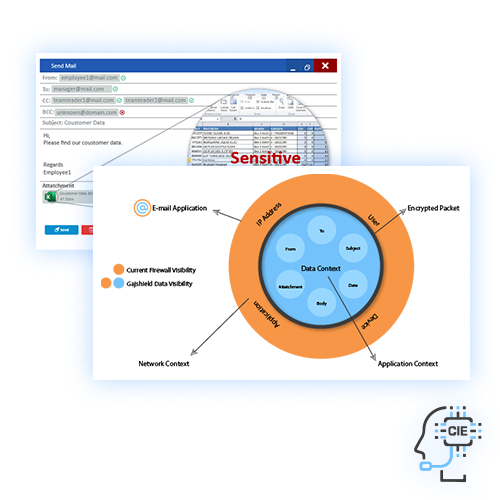
A Unique Context based
DATA LEAK PREVENTION
A Powerful
CONTEXTUAL INTELLIGENCE ENGINE
OUR BLOGS
The 1.4 TB Warning: Lessons from the Nike Breach for Cybersecurity Leaders
The recent data exfiltration event targeting Nike has sent ripples through the industry. With a staggering 1.4 Terabytes ...
The Wrong Place to Save Money: Security
Why “cheaper” security is silently the most expensive decision you’ll make Every business is under pressure to cut...
When a Partner Gets Breached - What It Means for Your Organization
In today’s connected business world, no company operates in isolation. We rely on partners, vendors, and consultants to del...
Don't choose just because we are Made-In-India
In today’s digital-first world, cybersecurity is more than a compliance checkbox — it’s a cornerstone of business c...
The 1.4 TB Warning: Lessons from the Nike Breach for Cybersecurity Leaders
The recent data exfiltration event targeting Nike has sent ripples through the industry. With a staggering 1.4 Terabytes ...
The Wrong Place to Save Money: Security
Why “cheaper” security is silently the most expensive decision you’ll make Every business is under pressure to cut...
When a Partner Gets Breached - What It Means for Your Organization
In today’s connected business world, no company operates in isolation. We rely on partners, vendors, and consultants to del...





