Why Upgrade to
Data Security Firewall?
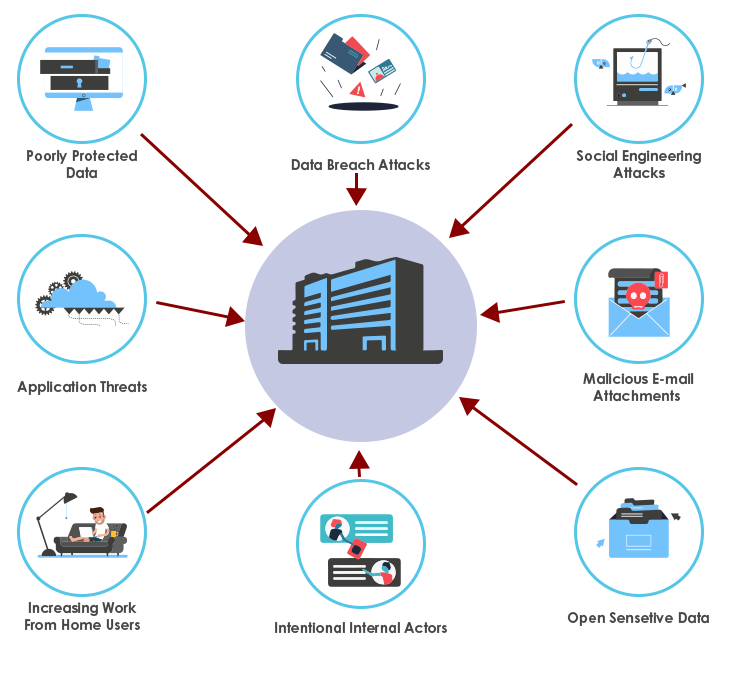
As it is said, “The world’s most valuable resource is no longer oil, it is Data.” The future of cybersecurity relies on securing data itself. Experts agree that securing data and preventing its exploitation is a top priority for CISO. The Data Security Firewall gives deeper visibility into data threat surface and allows to control data transactions and takes appropriate action to protect organization’s critical data being illicitly used and prevent exploitation, improving the overall health of data security in an organization.
Threats Have Evolved
Threat Surface Monitoring and Control

Data Security Firewall
The Data Security Firewall gives visibility into data threat that are critical to ensure Data Security. It uses a 2 stage categorization to give deeper understanding of the threat surface. It identifies policy violations and gives an overall data security health indication, helping in creating corporate and Data Security Policies for healthier data handling. It comprises of a Threat Heatmap that monitors violations and creates a real-time threat pattern that helps in quick identification of anomalies to act on, resulting in a stronger Data Threat Surface Monitoring and control.
Next Generation Firewall
Deeper Data Visibility

Data Security Firewall
The Data Security Firewall provides a detailed, granular and deepest possible data level visibility. The Data Security Firewall collects information on each transaction beyond just the traditional 7 Layers information including :
- Every piece of information that is transmitted to, from, and within the organizational network.
- The source and destination (E.g. URLs, email IDs, body content, subject, attachments, content of attachments etc.) of every inbound and outbound communication.
- Gains visibility on internet activities of computer devices used by the enterprise, which includes all the laptop computer devices used by employees from other remote locations.
Allowing the organization to deep dive into the granular details of transaction to generate reports and help setup data security policies at a granular level.
Next Generation Firewall
Approach Towards Security

Data Security Firewall
Next Generation Firewall
Integrated Context-Based Network Data Leak Prevention Solution
Data Security Firewall
Next Generation Firewall
Monitoring and Controlling SaaS
Data Security Firewall
Internal threats are commonly ignored threat type majorly caused by internal employees. These threats can be as simples not complying to enterprise’s security policies to a major data leak. The GajShield Data Security Firewall monitors for all activities and checks for Data Security Violations such as attempting to leak data using SaaS Cloud Application, attempting to use malicious website and applications that can result in threat to data security, trying to upload files on web, downloading malicious files, etc. and creates a violation report right at the dashboard for further action by the cybersecurity team.
Next Generation Firewall
The Next Generation Firewall does not looks into the Data threats caused by internal employees, its protection is restricted to general security violations only and fails to identify violations that are beyond its general network visibility. It does not provides a data security policy violation report.
Protection From Internal Threats

Data Security Firewall
Internal threats are commonly ignored threat type majorly caused by internal employees. These threats can be as simples not complying to enterprise’s security policies to a major data leak. The GajShield Data Security Firewall monitors for all activities and checks for Data Security Violations such as attempting to leak data using SaaS Cloud Application, attempting to use malicious website and applications that can result in threat to data security, trying to upload files on web, downloading malicious files, etc. and creates a violation report right at the dashboard for further action by the cybersecurity team.
Next Generation Firewall
The Next Generation Firewall does not looks into the Data threats caused by internal employees, its protection is restricted to general security violations only and fails to identify violations that are beyond its general network visibility. It does not provides a data security policy violation report.
Securing Roaming Users

Data Security Firewall
Roaming users are the most accessible and easy targets for a lot of attackers. Protecting them while they are out of organization’s secured network is most important as these users possess a lot of important data and can act as the gateway for cyber-attacks. Using Enterprise Cloud, we enforce roaming users to route all network traffic through the firewall at HO, bringing them under a secured network and enforce all Data Security Policies to help secure data possessed and prevent data leaks by these employees without impacting performance of the computer device.
Next Generation Firewall
The Next Generation Firewall protects only the employees within its secured network, once stepped out of the network, it becomes ineffective and fails to provide visibility of such roaming users and enforce security policies on them, leaving them as the most vulnerable entry point to the organization’s network for cyber attackers without having security solution in place.
Data Health Criticality Indicator

Data Security Firewall
The Data Security Firewall Features a Data Health Indicator that shows overall health of data in the organization. The data security firewall allows tagging of data security policies and It keeps an eye on data leaving the organization. Based on the criticality assigned to the data security policies, It generates report that indicates criticality of data being sent out of the organization using the various platform. It is first of its kind to have integrated data health indicator for organization to give an overview of data travelling out of the organization and help setup policies based on its observations. This not only helps organization to understand data usage but also help in curbing data leak.
Next Generation Firewall
The Next Generation Firewall works on the traditional perimeter level security and does not hold data as its core element for security, this restricts the firewall to gain visibility over data and fails to create a report that emphasizes on organization's data health, instead it relies on networks security for the overall security health of the organization which is considered to be vanishing today with organizations moving to a hybrid network infrastructure.
