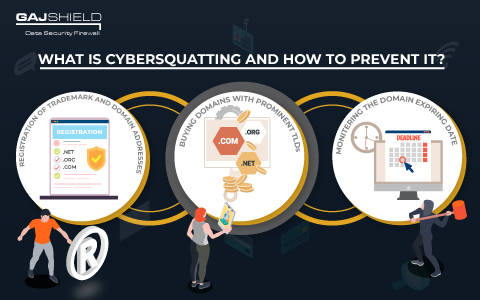
Cyber squatting, or domain squatting, is a specific cyber crime involving the imitation of domain names. These names are unauthorized creations that resemble other organizations or individuals’ domains with the intention to profit off their reputation or redirect the traffic to their own fraudulent domain.
October is recognized as Cybersecurity Awareness Month by the Cybersecurity and Infrastructure Security Agency (CISA). The theme for this year is “See Yourself in Cyber”, which emphasises that even though cybersecurity is a complex subject, it is ultimately about people.

The digital revolution has forced all industries to go online, one such industry was retail, and with it also came the emergence of e-commerce. With millions of people now using online shopping as the preferred method, retailers are privy to a host of information. This makes them a hubspot for hackers. Moreover, physical stores using software for monitoring, transactional process, and other services to store sensitive information are also facing threats.
Get In Touch With Us
Subscribe to our Newsletter
2025 © GajShield Infotech (I) Pvt. Ltd. All rights reserved.

