Preventing Identity Threats
Identifying an identity threat is crucial for enterprise as not recognising or ignoring it can be very dangerous and can lead to major loss and theft of critical data. Identity threats involve cybercriminals stealing the login credentials of your employees to gain access to your network and data. Hackers steal user identities either by tricking employees into revealing their details, having them install and run malicious software, or carrying out automated brute force attacks.

Several Canadian government services, including the National Revenue Agency, had to be disabled, in August 2020, following a credential stuffing attack that resulted in the hacking of more than 11000 accounts of the Canadian Revenue Agency (CRA) and other government services like the Government of Canada Key (GCKey) service. Having awareness about various cybersecurity threats, such as identity threats, can help create an effective contingency plan that can protect your enterprise from a myriad of cybersecurity issues. You can, therefore, create specific policies to safeguard against specific cybersecurity threats.
Let us look at how GajShield Data Security Firewalls helps in mitigating identity threats.
User Identity:
Using the Data Security Firewall, companies can enforce users to access enterprise network using a VPN connection from outside their security infrastructure, including from home, and implement policies that restrict connection attempts to a predefined number of incorrect password. Such initiatives help protect against brute-force attacks by limiting the number of attempts essential to prevent such identity breach attempts. The data security firewall also allows enterprises to have a password policy for all user to have a unique password for each user and avoid the use of a generic password to prevent credential stuffing across users. To enhance security, users can be provided multi-factor authentication using OTP which can be sent to them to prevent any unauthorised access to data. Enterprises can also limit the number of concurrent sessions for these users as an added layer of security. Authorisation based on time can further limit access to corporate assets on odd working hours preventing attackers to use work from home users as an entry point into their network.

Multi-Level Authentication
The Data Security Firewall can bring enterprise’s remote users under the firewall and enforce a data security policies on them that allow monitoring each and every piece of data transacted while controlling the use business and non-business platforms in the likes of the web, saas, mail, social media, etc. at granular context level e.g. preventing the use of Gmail from personal IDs and allowing access to official/business IDs only, restricting the personal use of these platforms to prevent both intentional and unintentional uploads of critical data on them, resulting in data exploitation. The Data Security Firewall achieves this by applying security to the Data itself against applying security at a perimeter level, protecting and maintaining the enterprise’s data security health at all times while protecting from the entire threat surfaces.

Bringing Remote/WFH Users under Security Infrastructure
The Dashboard of the Data Security Firewall reports any attempts to violate these enterprise’s data security policies using a violation categorization feature allowing to assign criticality level to these policies and a health indicator to indicate enterprise’s data security health with other important information for the security admins to take quick actions to protect critical data being exploited.
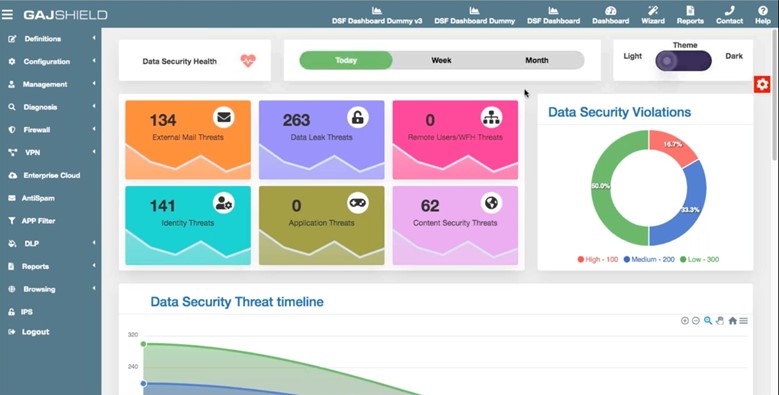
GajShield Data Security Dashboard
Enterprises need to adopt a security approach that relates all these security measures with data security to protect themselves against various data threats. GajShield’s data security firewall provides visibility on an enterprise's data threat plane with detailed drilled-downed reports on such identity threats, allowing them to be controlled and features a security heatmap that creates a real-time incident graph, providing necessary information for security admins to take definitive action.
Get In Touch With Us
Subscribe to our Newsletter
2025 © GajShield Infotech (I) Pvt. Ltd. All rights reserved.
