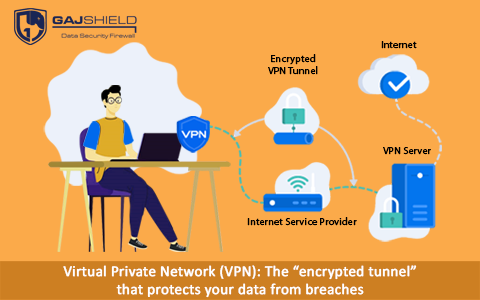
The fear of being watched and your data being illegally accessed by malicious entities somewhat spoils the experience of using the internet. As you know, entering the world wide web leaves users vulnerable to nasty cyber threats such as phishing, ransomware and DDoS attacks that can lead to losses in terms of money
Consumerism has made personalised marketing a necessity for nearly all kinds of businesses. For personalising their marketing campaigns, such businesses collect and analyse the data of their target audience from various sources—purchase records, social media data, and a few others. Possessing so much valuable and sensitive data makes the databases of organisations vulnerable to cyber

Out of the 1.4 million cases of identity theft reported in 2020, nearly 4,00,000 fell under credit card fraud. This represents a whopping 44.6% increase over 2,71,927—the instances of credit card fraud-based attacks in 2019. Needless to say, credit card fraud, a data security threat that involves malicious
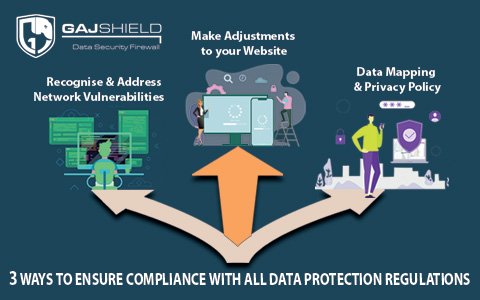
As the value and significance of data have risen through the last decade, the number of laws to regulate data collection and usage has also increased manifold. Gradually with time, such laws have become increasingly stringent. Additionally, organisations leave themselves vulnerable to massive penalties and other types of punitive action if they fail to comply with such laws
Get In Touch With Us
Subscribe to our Newsletter
2025 © GajShield Infotech (I) Pvt. Ltd. All rights reserved.
